In 2023, Cybersecurity is high on the agenda for IT departments: security protocols, ISO certifications, cyber platforms and other risk management initiatives are now becoming a major cost within IT departments. It seems not a week goes by when we don’t hear about a significant data breach, large scale DDoS attack or other hacking attempts. It’s clear that no business is exempt from attacks. It’s no wonder so many businesses are reprioritising cybersecurity. Rightly so. According to the Australian Cyber Security Centre, 144 cyber crimes are being reported by businesses daily – that’s 1 every 10 minutes.
Conversely, value-driving projects – the ones generating dollars and cents – have been temporarily paused to respond to un-budgeted, critical cybersecurity tasks. So, in a year where many businesses were seeking to rationalise IT expenditure, high risk security events requiring urgent remedial action have stretched already limited IT budgets. Let alone other prevailing market forces limiting growth building exercises through digital innovation.
As we hear the challenges of CIO’s and CTO’s nationally, we like to quietly remind everyone that opportunity may be seen in risk (although it’s often the opposite that is articulated).
In this spirit, let us consider: what additional value can we derive from our cybersecurity efforts?
The cyber afterthought
For far too long, digital projects have been delivered with security left as an afterthought requiring web developers to deploy an entire security layer, set of protocols and supporting infrastructure to secure the developed solution. All delivered in a very short timeframe towards the end of a project.

DIAGRAM 1: High-level view of “most” digital projects where application security measures are taken rapidly and late in a project
It’s a problem that leads to half baked security solutions and patches. Often, a higher Total Cost of Ownership is realised when ongoing vulnerabilities are identified in technology stacks requiring tech teams to blow the dust off out-of-date documentation, take urgent remedial action, perform rounds of testing and then release patches into live environments. Such exercises can be costly and pull focus away from profit making transformation exercises.
In defence of web and application development teams, most teams will do a great job of following best practice security standards. A common model is illustrated below.
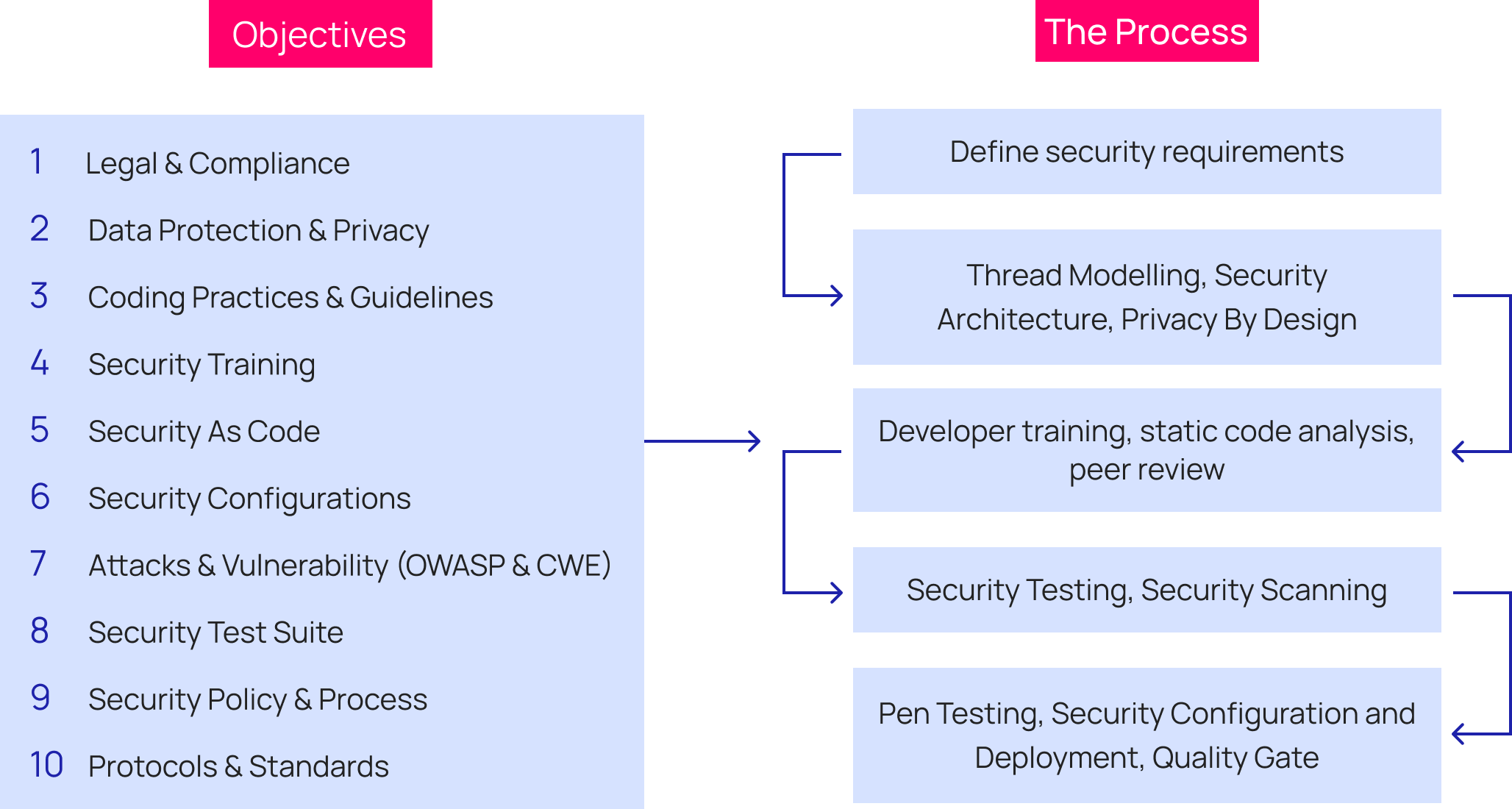
DIAGRAM 2: Standard application security framework
But this leads to another question: are developers solely responsible for application security? When network engineers are pouring water over digital assets under attack, their common response would be ‘no’.
In fact, our security framework example (see Diagram 2) has significant shortcomings, as it does not:
- proffer ideal user experiences with seamless security and privacy functions;
- communicate the importance of security and user data privacy inline with an organisation’s values;
- educate internal or external application users in protecting their credentials and using the available security methods (eg. MFA); or
- effectively describe to audiences why they should trust a brand’s digital systems.
One may observe that each of these items are user-centric in nature. They talk to design considerations, communication, and education.
Therein lies the opportunity for technology chiefs to reconsider where security fits into the value chain in digital projects to avoid the tug of war between digital innovation (opportunity) and cyber (risk).
Embedding cybersecurity in your digital innovation and transformation projects
Experience tells us that there is great value in engaging users during the planning, scoping and design phases of any digital project in order to enrich user experiences for all audiences – customers, staff, members, or otherwise. Design Thinking methodology aims to solve problems with the target audience in mind – often broken down into segments or personas. This type of human-centric approach helps us understand and empathise with our intended users. It makes for a great platform to commence the discussion around systems security.
During the planning, discovery and design phases is the perfect time to embed a set of security-centric tools and methods where we can effectively explore the value of security in the context of the broader application experience.
In the below chart, we introduce the concept of a “secure digital project framework” to highlight the types of exercises that offer ways to consistently consider cybersecurity.
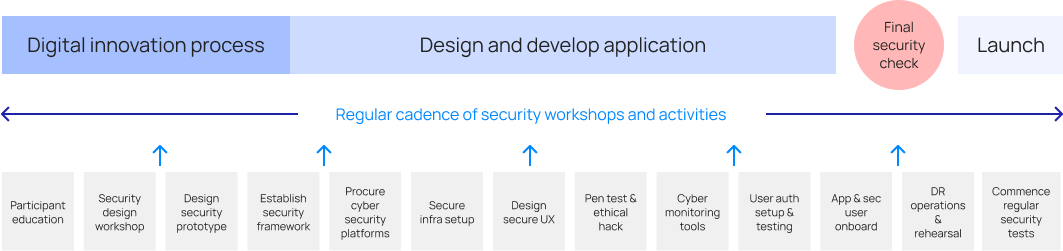
DIAGRAM 3: Example of “Secure Digital Project” framework includes regular cybersecurity workshops and actions throughout the project lifecycle
Here we seek to take all participants along for the ride with consistent and regular security-conscious conversations. Initially, a briefing session should include cybersecurity education to lift our team members to a common understanding. During discovery we may ask our team members to consider the following: Where will application data be stored? Who will have access to it? Why will customers entrust us with this data? What sort of access methods will build or reinforce trust in our brand and our digital platforms? How can we offer our customers a seamless user experience?
Solution Architects and Business Analysts should be listening intently to these preliminary security-focused conversations to capture and convert these ideas into business requirements that may be assessed for feasibility during formal scoping. Technology specialists may then connect the dots between applications, databases, hosting environments, API’s, cyber security tools and compliance requirements. By the time designers get involved, the discovery process should hold sufficient wisdom to inform well-designed and low friction user experiences such as user account management, OTP, KYC, content/data sharing permissions, and so forth.
When it’s time to plan the launch of our digital product, marketing teams will want to tease out the value statements that authentically describe the application’s data privacy standards and any application security methods. If organisational change is required, L&D departments may wish to elaborate on security protocols to educate users on security best practices. It’s not hard to see what value cross-functional team members can bring to the table. Their insight and perspective can help digital teams deliver richer experiences for users of all types.
As with any framework, however, it is simply a set of guidelines rather than a prescriptive blueprint. In reality, a suite of project tools may be tailored to facilitate regular cybersecurity discussions or exercises so that cyber is not only embedded in the process, but delivered.
Using a rough formula, an organisation may wish to consider a 10% project overhead in cybersecurity methods and processes to earn the possibility of exponential savings in future by mitigating the risk of data breaches, DDoS, or other attacks. This approximation is entirely dependent on factors such as cybersecurity resource costs and technology composition. Deloitte suggests 10% is a good starting point.
What does a data breach cost these days, anyway?
The average cost of a data breach in Australia is $3.35 million per breach, an increase of 9.8% year on year. This average figure will increase next year as the Australian Federal Government introduces tougher data breach penalties in response to the devastation of the Optus breach. This legislation plans to increase the penalty for serious or repeated data privacy breaches to $50 million, or 30% of a company’s adjusted turnover in the relevant period, whichever is greater – a significant increase from the former penalty amount of $2.22 million.
(source: https://www.upguard.com/blog/australian-data-breach-stats)
The risks are hard to ignore.
What users really want
Customers want to engage with brands that respect and protect their data while transparently communicating privacy and security policies. In the past, many users have held the opinion that security is a necessary evil. Users describe ‘password hell’ as the bane of existence. But now customers are expecting more. PWC reports 85% of [surveyed] customers say that they will not do business with a company if they are worried about its data practices.
Imagine, for a moment, all your medical information or phone account data is leaked onto the dark web and suddenly you’re receiving daily calls from scammers. Unthinkable, right?
As users of technology, our mindset on the value of our personal and corporate data has fundamentally changed forever. This reinforces the need for digital technology ‘makers’ to design and embed effective security systems and protocols that instil trust and confidence in users.
This author can think of a number of active project engagements where user security and identity management have a quantifiable impact on customer engagement and conversion ratios. When building customer portals, e-commerce experiences, member application forms, and lead funnels to name a few, marketers, designers and developers have a large role to play in their performance. Web experiments, customer surveys and user behaviour platforms provide us with the tools we need to optimise security components within each of the experiences. Suddenly, we’re considering cybersecurity beyond the project delivery phase – opportunities to yield continuous value from our cybersecurity efforts may be realised throughout the entire lifecycle of any given digital product.
The intersection of opportunity and risk.
If we can successfully bridge the gap between digital innovation as opportunity and cybersecurity as risk management, we might find more than peace of mind for boards and execs signing the cheques on digital projects. We may find ways to differentiate in the market, out-perform competitors, win consumer trust, add real outcomes to our Corporate Social Responsibility charters, improve online commerce funnels and conversion ratios, deliver on system up-time KPI’s, and even reduce IT systems support costs.