There are many cybersecurity issues that large companies may face, and the most critical ones can vary depending on the industry, company size, and other factors. However, based on recent trends and observations, the three most critical cybersecurity issues being faced by the management of large companies are:
- Data Breaches: Data breaches can result in the theft of sensitive customer or corporate data, such as personal identifiable information (PII), financial data, intellectual property, or trade secrets. These breaches can be carried out through various means, such as phishing attacks, malware infections, or exploiting vulnerabilities in the company’s systems. Data breaches can cause significant financial losses, damage to the company’s reputation, and even legal liability.
- Ransomware Attacks: Ransomware attacks involve malicious software that encrypts a company’s files, rendering them inaccessible, and then demands a ransom payment in exchange for the decryption key. These attacks can result in significant downtime, loss of critical data, and reputational damage. The financial cost of ransomware attacks can be substantial, with ransom payments, recovery costs, and potential regulatory fines.
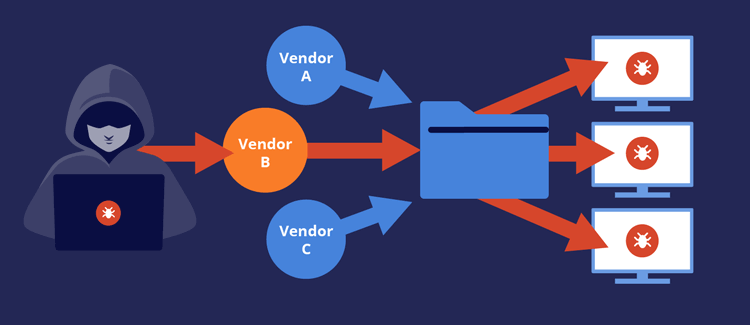
- Supply chain Attacks: Supply chain cybersecurity is indeed another significant issue that large companies are facing today. Large companies often rely on a complex web of suppliers, vendors, and third-party service providers, which can create new entry points for cybercriminals to exploit. A cyberattack on a single supplier can have a cascading effect, leading to a compromise of the entire supply chain. A cyberattack on a single supplier can have a cascading effect, leading to a compromise of the entire supply chain.
In this article I am only going to refer to #3 – Supply Chain Attacks.
Some of the most notable and highest profile supply chain data breaches are:
- SolarWinds (2020): One of the largest supply chain breaches in history was the SolarWinds hack, which was discovered in December 2020. The breach affected multiple government agencies and private sector organizations. The attackers were able to compromise the SolarWinds software supply chain, which is used by many organizations to manage their IT infrastructure.
- Target USA (2013): In 2013, Target suffered a massive data breach that affected over 110 million customers. The breach was initiated through a third-party vendor that had access to Target’s payment system. The attackers were able to gain access to the
vendor’s network, which allowed them to steal Target’s customer data. - NotPetya (2017): The NotPetya malware attack in 2017 was initially thought to be a ransomware attack. However, it was later revealed to be a supply chain attack that targeted the Ukrainian software firm MeDoc. The attackers were able to compromise
MeDoc’s software update mechanism, allowing them to distribute the malware to MeDoc’s customers, which included many global organizations. The attack caused widespread damage, with estimated losses in the billions of dollars. - CCleaner (2017): In 2017, the software company Avast discovered that the popular CCleaner software had been compromised. The attackers had inserted malicious code into the software update mechanism, allowing them to distribute malware to over 2.27
million users. The attack was attributed to a nation-state actor, and the motive behind the attack is still unknown. - Marriott (2018): In 2018, Marriott suffered a data breach that affected up to 500 million customers. The breach was initiated through a third-party vendor that provided guest reservation software to Marriott. The attackers were able to gain access to the vendor’s network, which allowed them to steal Marriott’s customer data.
As large companies continue to rely on a multitude of suppliers for their business needs, the risk of cybersecurity breaches through the supply chain continues to grow. Cyberattacks on a single supplier can compromise the entire supply chain, potentially leading to significant financial loss, reputational damage, and legal liability. Therefore, it is essential for large companies to ensure that their suppliers have robust cybersecurity measures in place to safeguard their digital assets. This article provides an in-depth analysis of the steps large companies should take to mitigate cybersecurity risks associated with their supply chain logistics.
Develop a Comprehensive Cybersecurity Policy
The first step that large companies should take is to develop a comprehensive cybersecurity policy that outlines the minimum-security requirements for their suppliers. This policy should include guidelines for securing data, networks, systems, and applications. The policy should also specify the security controls that the suppliers must implement and the frequency of security assessments. The cybersecurity policy should be based on industry best practices and international standards, such as ISO 27001 or The Australian Cyber Security Centre (ACSC) has developed a cybersecurity framework for Australian organizations known as the Essential Eight. The policy should be tailored to the specific needs of the company and its suppliers, taking into account the industry, the size of the
company, and the types of data that will be shared.
Establish Security Requirements
To ensure that their suppliers meet the minimum-security requirements, large companies should establish specific security controls. These controls may include:
- Multi-Factor Authentication: Multi-factor authentication (MFA) is a security mechanism that requires users to provide two or more factors of authentication before accessing a system or application. This can include something the user knows (such as a password), something the user has (such as a token), or something the user is (such as a biometric). MFA can significantly reduce the risk of unauthorized access, even if the user’s password is compromised.
- Encryption: Encryption is the process of encoding data in a way that only authorized users can read it. Encryption can be used to protect data in transit or at rest. For example, data can be encrypted before it is transmitted over the internet, or it can be encrypted when it is stored on a device. Encryption can help prevent unauthorized access to data in case of a breach.
- Intrusion Detection and Prevention: Intrusion detection and prevention systems (IDPS) can be used to detect and prevent unauthorized access to a system or network. IDPS can analyse network traffic, detect suspicious activity, and block potential threats. IDPS can help prevent attacks such as distributed denial of service (DDoS) or malware infections.
- Endpoint Protection: Endpoint protection is a set of security solutions that protect endpoints (such as desktops, laptops, and mobile devices) from malware and other security threats. Endpoint protection solutions can include antivirus software,
firewalls, intrusion prevention, and application control. Endpoint protection can help prevent attacks that target vulnerabilities in endpoint devices. - Data Handling Procedures: Large companies should establish specific procedures for handling sensitive data, such as personally identifiable information (PII), financial data, and intellectual property. Data handling procedures should include data
classification, storage, and transmission. Sensitive data should be stored and transmitted securely, and access should be limited to authorized users.
Conduct Regular Assessments
To ensure compliance with the security policy and requirements, large companies should conduct regular assessments of their suppliers cybersecurity posture. Assessments can be done through questionnaires, on-site inspections, or third-party assessments.
The assessment should evaluate the suppliers network architecture, security controls, and data handling procedures. The assessment should identify any vulnerabilities or weaknesses in the suppliers cybersecurity posture and provide recommendations for improvement. The assessment should also evaluate the suppliers incident response plan, including procedures for detecting, reporting, and containing security incidents.
Provide Security Training
Large companies should provide cybersecurity training to their suppliers employees to ensure they are aware of potential risks within their organisation.
Implementation Time
The time it takes for a large company to implement good supply chain cybersecurity strategies can vary widely depending on a number of factors, including the company’s current level of cybersecurity maturity, the size and complexity of its supply chain, and the resources available to the company for implementing these strategies. For a large company that has already established a cybersecurity program and has some level of experience with supply chain cybersecurity, implementing good supply chain cybersecurity strategies can take a few months to a year. The company would need to evaluate its current supply chain cybersecurity posture, develop policies and guidelines, establish security requirements, and conduct assessments of its suppliers. The company would also need to provide security training to its suppliers employees, monitor third-party access, create an incident response plan, and establish data sharing agreements.
However, for a large company that has not yet established a cybersecurity program or has little experience with supply chain cybersecurity, the timeline for implementing good supply chain cybersecurity strategies could be longer. The company would need to first establish a cybersecurity program, including policies, procedures, and guidelines. It would then need to evaluate its current supply chain cybersecurity posture, develop and implement cybersecurity controls, and assess the cybersecurity posture of its suppliers. This could take up to two years or more, depending on the size and complexity of the company and its supply chain.
It’s worth noting that implementing good supply chain cybersecurity strategies is an ongoing process that requires regular assessments, monitoring, and updates to policies and controls. Cyber threats are constantly evolving, and new vulnerabilities can emerge in a company’s supply chain at any time. Therefore, companies must remain vigilant and continuously adapt their supply chain cybersecurity strategies to stay ahead of the threat landscape.
In conclusion, the time it takes for a large company to implement good supply chain cybersecurity strategies can vary widely depending on its current level of cybersecurity maturity, the size and complexity of its supply chain, and the resources available to the company for implementing these strategies. However, regardless of the time it takes to implement these strategies, it is essential for
large companies to take a comprehensive approach to supply chain cybersecurity to mitigate the risk of cyber attacks and maintain business continuity.